How Parents Can Hack An Android Cell Phone

There are a number of legitimate reasons you should want to know how to hack android phones. Maybe you have children you need to monitor or employees you suspect of stealing. Whatever the case may be, in this article we will show you how to hack Android phone and prevent yourself from being hacked.
The best way to can gain access is by using a spy app. These apps allow you to hack into Android and do things like activate the microphone, intercept calls, and view all social media activity.
How To Hack A Android Phone
There are several methods that can be used to hack into an Android cell phone. For most parents, the only realistic method is using spy apps as they are readily available, proven, and legal (when used as appropriately).
When trying to ensure the online safety of your children, knowing the methods used to gain unauthorized access to devices can be invaluable. Understanding how hackers operate can give you insights into protecting your family's data better and put protective measures in place. For those reasons, we will discuss more advanced and isoteric hacking methods below.
Spy Apps
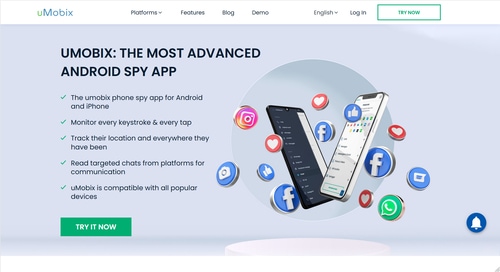
Spy apps are designed to run quietly in the background, gathering information without alerting the user. With these hacking apps, you can easily gain control and be able to access their files remotely. They have the ability to not only track people, but also to penetrate and monitor the phone's data. You can remotely monitor more than 39 data categories, including GPS position, call logs, text messages, contact lists, social media, and other application data.
uMobix
uMobix is a comprehensive digital monitoring tool designed primarily for parental control. It's easy to use, quick to install, dependable, and stays hidden. Here's how you can use it:
- Purchase the uMobix subscription: Start by purchasing the a plan from uMobix that best suits your requirements. The subscription packages are flexible and cater to different needs.
- Install the app: After you have chosen a plan, you'll receive an email with installation instructions. You need to follow these steps on your child's phone to install the app.
- Start Monitoring: The app will function in stealth mode, meaning it won't show up on the list of applications. Once installed, the app starts collating data and sending detailed reports to an online control panel where you can see everything.
Apart from tracking call logs and text messages, one unique aspect of uMobix is its ability to recover deleted messages, making sure parents don't miss out on any critical information. It also provides social media tracking (Facebook, Instagram, Snapchat), GPS location tracking, email checks and even monitors internet usage and installed apps.
This approach ensures parents get all-round information about their child's actions online, helping them identify any threats their children could be exposed to or behavior changes that need intervention.
- Camera activation
- Can stream live video
- Microphone activation
- GPS tracking
- Can spy without the user knowing
- Data retention limited to 30 days on the basic plan
mSpy

mSpy is another dynamic tool that equips parents with essential insights into their kid's smartphone activities. Here's how you can set up mSpy:
- Select a Subscription Plan: mSpy offers multiple plans depending upon various needs that range from basic text and call log monitoring features to comprehensive packages offering social media tracking, keylogging, and more.
- Create your mSpy account: Once purchased, you'll be asked to create your personal mSpy account where all the extracted data will be accessible remotely via an online dashboard.
- Install mSpy: The next step involves setting up mSpy on the target Android device which requires short-term physical access for installation purposes.
Once successfully installed mSpy silently operates in stealth mode which is invisible to users while efficiently extracting all relevant information, including logging all incoming/outgoing calls, recording actual call conversations selectively (if using mSpy Extreme), and logging SMS/MMS messages.
Additional features include real-time GPS location tracking, geofencing, and browsing history.
- Logs text messages
- Keylogger & Screen recorder
- Real-time GPS tracking
- Geofencing
- Access all social media apps
- Lacks camera activation
Phishing Attacks
Phishing attacks are achieved by tricking someone into clicking a malicious link or with fake login pages to capture user credentials. These attacks are typically initiated via email or text messages that look legitimate but contain harmful content meant to deceive. They are most effective against less technically savvy targets. As a parent, educating your child about security attacks, recognising suspicious links or emails, and not sharing their credentials can make them safer online.
SS7 Vulnerability Exploitation

SS7 or Signalling System Number 7 is a telecommunication protocol defined by the International Telecommunication Union (ITU). This system allows cellular networks around the globe to communicate with each other for passing calls and messages between networks; however it has several built-in vulnerabilities that hackers may exploit with intensive knowledge and specialised equipment.
Demo: How An SS7 Attack May Be Conducted By A Rogue Hacker:
- The attacker gains access to the global SS7 network with an STP (Signal Transfer Point).
- The attacker sends requests like "Provide subscriber information" using targeted mobile signalled services numbers (MSISDNs). After getting a roaming MSC/VLR (mobile switching center/visitor location register) address an attacker can use SRI-for-SM queries (Short message service routing information) which return IMSI & MCC-MNC if HLR in question allows this operation.
- A hacker might use this technology track down a particular person's exact location exploiting the IMSI identified previously via global MSC/VLR number responses on MAP ATI invoke packets.
- The attacker can now further exploit retrieved information by faking subscriber's SIM card or injecting malicious code via fake OTA messages doing things like listing received/sent/dialed calls & SMS content, and even gain remote command execution capabilities on target phones in a worst case scenario.
CSPloit
CSPloit is a popular application hackers use for smartphone attacks. Similar to ZAnti, this program can only access rooted Android devices.
Numerous ethical hackers adore it due to its vast array of capabilities, which include DNS spoofing, password sniffing, forging TCP/UDP packets, and hijacking web sessions.
Fing Network Tools
Fing Network Tools is a powerful network scanner that can analyze connections. The objective is to enhance speed and performance via specific characteristics.
Users can view and manage connected devices, as well as permit or deny access. Additional possibilities include identifying all devices connected to a WiFi hotspot and advanced smartphone analysis that can be useful for monitoring phones.
Hacking Android For Free With Google Maps

You could also use Google Maps to track an Android device. If the GPS service is enabled, you can see where the Android has been as well as where it is now. You can use Google Maps to view historical or real-time location tracking. However, you must sign in with your account and allow reporting, logging, and GPS on the target Android.
This is how you find out where a Android is by using Google Maps:
- Navigate to "Settings" and then "Location Services."
- Launch "Google Maps" and then click the "Menu" button.
- You will notice a pop-up prompting you to "Share your current location".
- Choose "Until closed", then click "Select Person".
- Select your name from this list and you will be notified of the target's whereabouts.
- If you do not see your account listed, you can select your mobile number and click "Share via connection" in the pop-up window.
What you will notice is that none of the alternative methods will beat installing spy software.
Understanding The Android Operating System
To effectively explore the security technology found on an Android, comprehending the fundamentals of the Android Operating System is essential. Android, being open-source, offers greater customization but may also, unfortunately, be more prone to potential security holes. Discerning its security features can provide a better understanding of how weaknesses can be exploited for ethical hacking.
The Principle of Vulnerabilities
Software vulnerabilities are loopholes or weaknesses that may be exploited by hackers. Given the variety of apps, updates, and phone manufacturers in the Android ecosystem, vulnerabilities can originate from many sources. Although Google continually works to patch these vulnerabilities, new ones can arise with new software developments and recognizing these can be crucial for ensuring digital safety.
Is It Legal?
Generally, it is legal to hack devices you own. The issues arise from having the permission of the user. Many jurisdictions allow hacking a device you own even if the person using it is unaware.
Laws can vary greatly by state and country, and penalties can be severe, so do not hack anything before consulting a lawyer. More than the technical steps, this is the most important component of monitoring any device.
Conclusion
There are numerous methods for hacking Android. In this tutorial, we've investigated and analyzed approaches ranging from simple to quite sophisticated in-depth. Keep in mind, however, this information is intended solely for research purposes.
Therefore, we strongly advise you to utilize only legal and ethical tactics. Otherwise, you could face legal repercussions. When doing so, check your local laws and confirm that using these applications is legal.